Access Problems Usually Look “Normal” Until They Are Not
Many security incidents do not start with someone breaking down a digital door. They start with a login that should not have worked. It might be a former employee whose account was never fully removed, a shared password that got reused too many times, or an admin account that was used for everyday work and eventually got compromised.
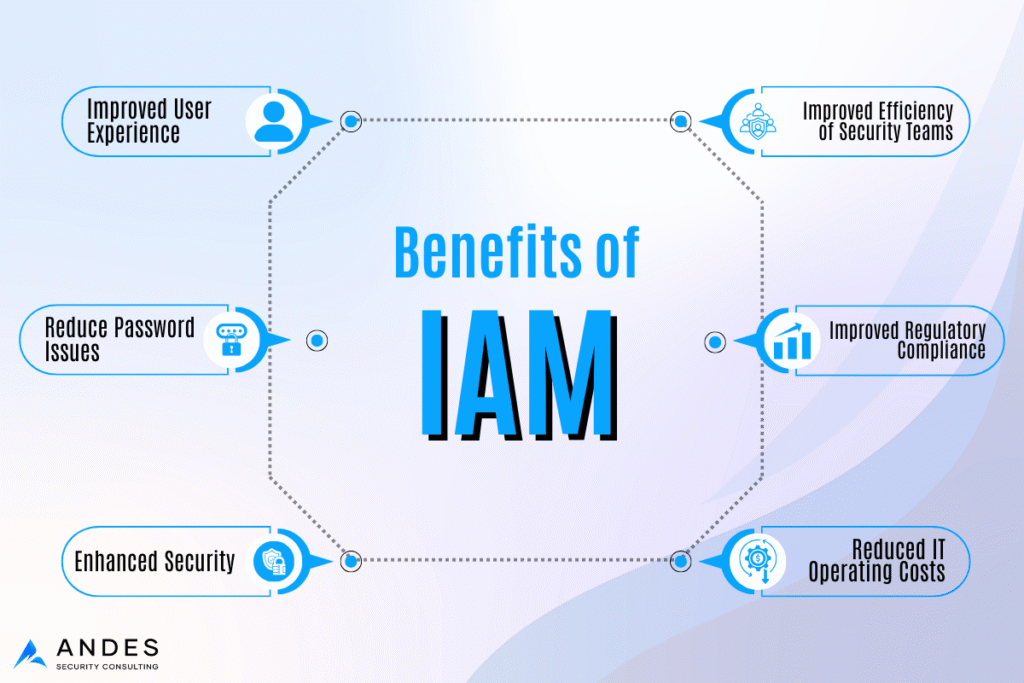
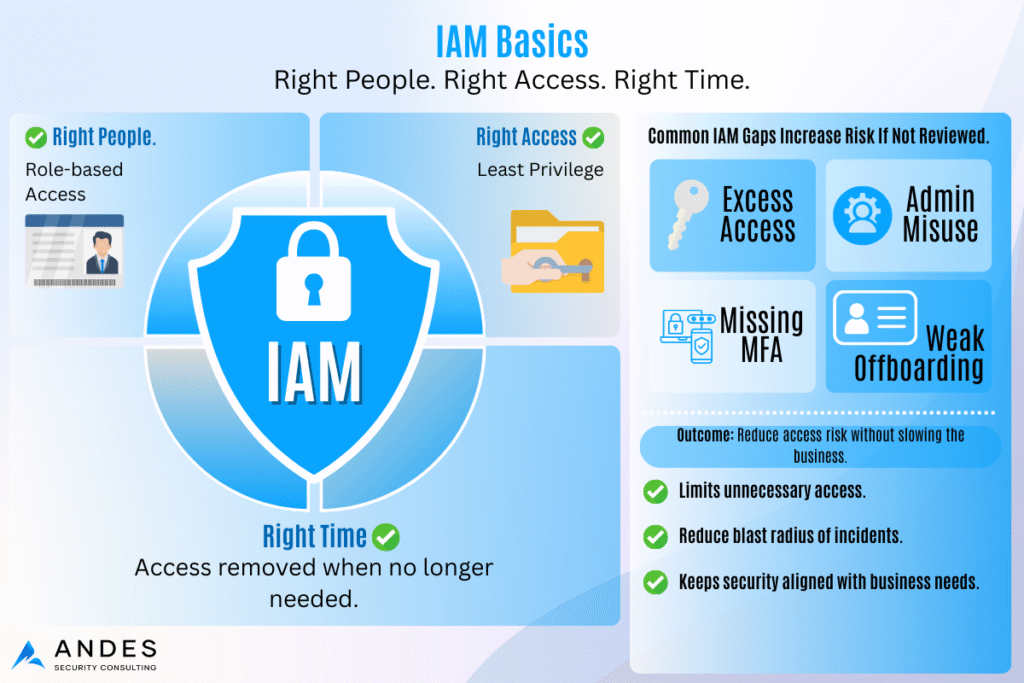
That is why Identity and Access Management (IAM) matters. IAM is simply making sure the right people have access to the right systems for the right amount of time. When it is working well, people can do their jobs without friction, and the business is not constantly exposed to unnecessary risk. When access isn’t properly governed, small missteps quickly become major risks — excessive access amplifies both errors and the impact of potential compromises.
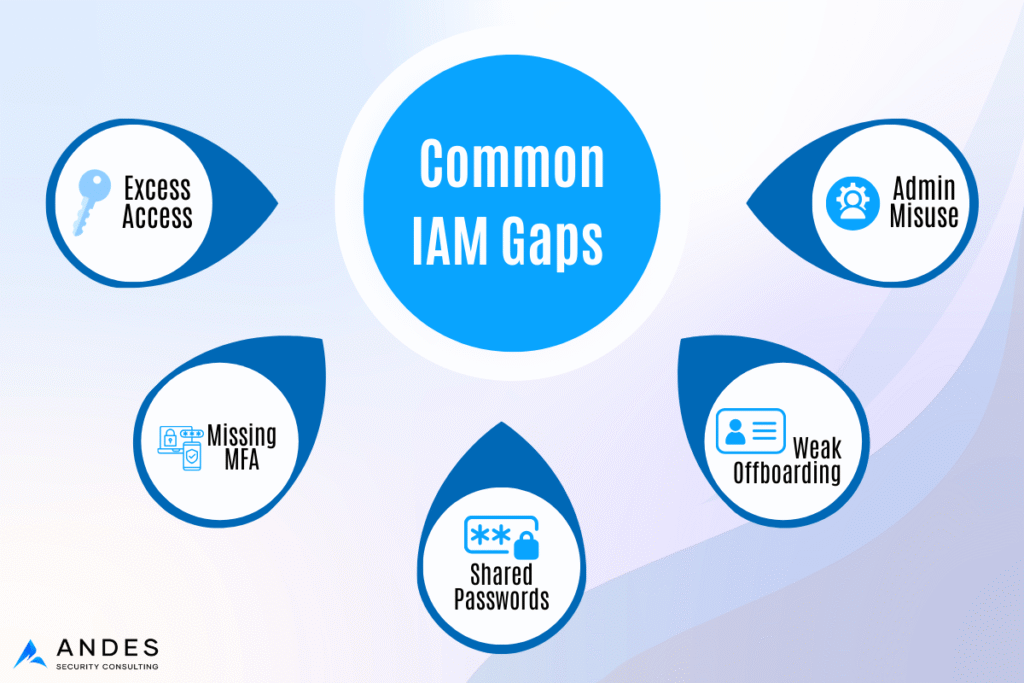
The Most Common IAM Gaps are Simple and Fixable
- The first common issue is that excessive access becomes the default. As companies grow, access is often granted quickly to keep work moving, but rarely reviewed or revoked later. Roles change, teams shift, new tools are added—and permissions accumulate over time. A simple way to reduce this risk is to review access based on roles and remove privileges that are no longer required.
- The second issue involves the misuse of administrative privileges. Admin access is highly powerful and should never be used for routine email or day-to-day activities. If an admin account is compromised, the impact is significantly greater than a standard user breach. A practical solution is to use separate admin accounts exclusively for elevated tasks while keeping everyday work on standard user accounts.
- Another significant gap is inconsistent multi-factor authentication (MFA). In many organizations, MFA is enabled for some systems but not others, and administrators may not have the stronger protections they require. Consistent MFA is critical—it prevents the vast majority of automated account-compromise attempts when applied uniformly.
- Offboarding user accounts is another common weakness. When employees leave, their access often remains active longer than it should. Accounts should be disabled immediately, active sessions and tokens revoked, and access removed from cloud applications, shared drives, and third-party tools.
- And finally, Shared accounts and shared passwords also create serious risks. They eliminate accountability, complicate investigations, and increase the likelihood of repeated incidents. Whenever possible, organizations should use individual user accounts and manage service credentials securely.
How Growing Business Should Approach IAM
Many organizations only review access after something goes wrong. A far better approach is to conduct regular access reviews, so privilege creep and stale permissions are identified early. Even quarterly reviews can significantly reduce access-related risk by highlighting users who have permissions they no longer need, and ensuring corrective changes are implemented.
A structured IAM review provides visibility into who has access to what, uncovers risky or excessive permissions, reduces the impact of compromised accounts, and establishes clear access rules as the business scales. The goal of IAM is not to slow people down—it’s to minimize unnecessary risk while keeping operations running smoothly.
If you’re unsure whether access in your environment aligns with how your business actually works today, an IAM review can quickly expose gaps and give you actionable next steps.
Contact us to schedule an access review and receive practical, right-sized guidance tailored to your organization.