Why It Matters and How to Get Started
By Andes Security Consulting
Cyberattacks targeting small and mid-size businesses (SMBs) have surged more than any other segment over the past three years. The shift to cloud platforms, remote work, SaaS adoption, and expanding digital footprints have made it easier than ever for attackers to exploit gaps in identity, access, and network controls.
For organizations with limited IT resources, protecting the environment has become increasingly complex — and traditional perimeter-based security is no longer enough.
This is where Zero Trust becomes not just a framework, but a necessity.
What is Zero Trust — and Why Should SMBs Care?
Zero Trust is a cybersecurity strategy that operates under one core principle:
“Never trust, always verify.”
Instead of automatically trusting users, devices, or applications inside the network, Zero Trust evaluates every access request continuously — regardless of where it originates.
For SMBs, this matters because:
- Most breaches start with compromised credentials
- Employees now access systems from anywhere, on any device
- Cloud adoption has eliminated clear network boundaries
- Attackers specifically target smaller organizations with weaker controls
- Lateral movement inside the network is easy when trust is assumed
Zero Trust reduces the attacker’s ability to move freely once they get in — and drastically narrows the blast radius of any breach.
Why Zero Trust Is Especially Critical for SMBs
Large enterprises have deep security budgets, SOCs, and mature tooling.
SMBs don’t — and attackers know this.
Zero Trust helps small and mid-size firms:
1. Reduce cybersecurity risk without massive budgets
Zero Trust is built on policies, identity controls, and segmentation, not expensive hardware.
2. Protect remote and hybrid workforces
Every user and device must authenticate continuously — no blind trust.
3. Minimize the impact of compromised credentials
Stolen passwords become far less useful when access is dynamically restricted.
4. Strengthen cloud and SaaS security
Zero Trust is cloud-native and aligns with the way modern businesses operate.
5. Meet cyber insurance and compliance expectations
Insurers and auditors increasingly require Zero Trust-aligned controls.
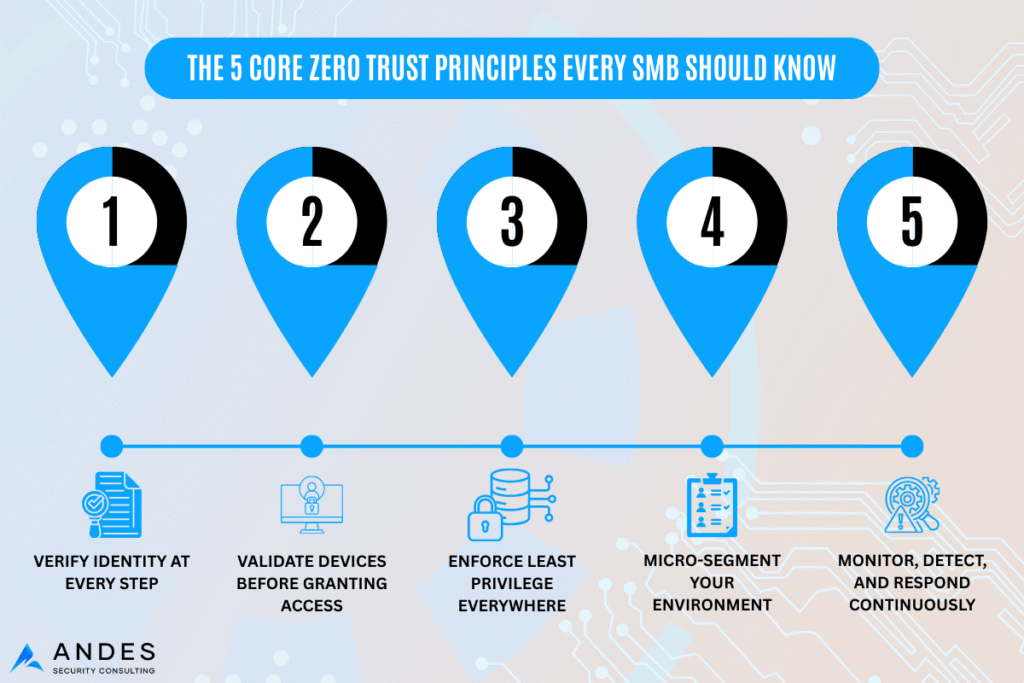
The 5 Core Zero Trust Principles Every SMB Should Know
You don’t need to implement Zero Trust overnight. Start with these foundational principles:
- Enforce multi-factor authentication (MFA)
1. Verify Identity at Every Step (Strong IAM/MFA)
- Use Single Sign-On (SSO)
- Implement role-based access control (RBAC)
2. Validate Devices Before Granting Access
- Ensure devices meet security baselines
- Block outdated or non-compliant endpoints
3. Enforce Least Privilege Everywhere
Users get only the minimum access required — nothing more.
4. Micro-Segment Your Environment
Divide your network and cloud resources into smaller trust zones.
If one system is compromised, attackers cannot move laterally.
5. Monitor, Detect, and Respond Continuously
Zero Trust is not set-and-forget.
It requires continuous logging, analytics, and automated response.
Zero Trust Health Check: What SMBs Can Evaluate Today
To help SMB leadership quickly identify gaps, here are practical, self-assessment questions:
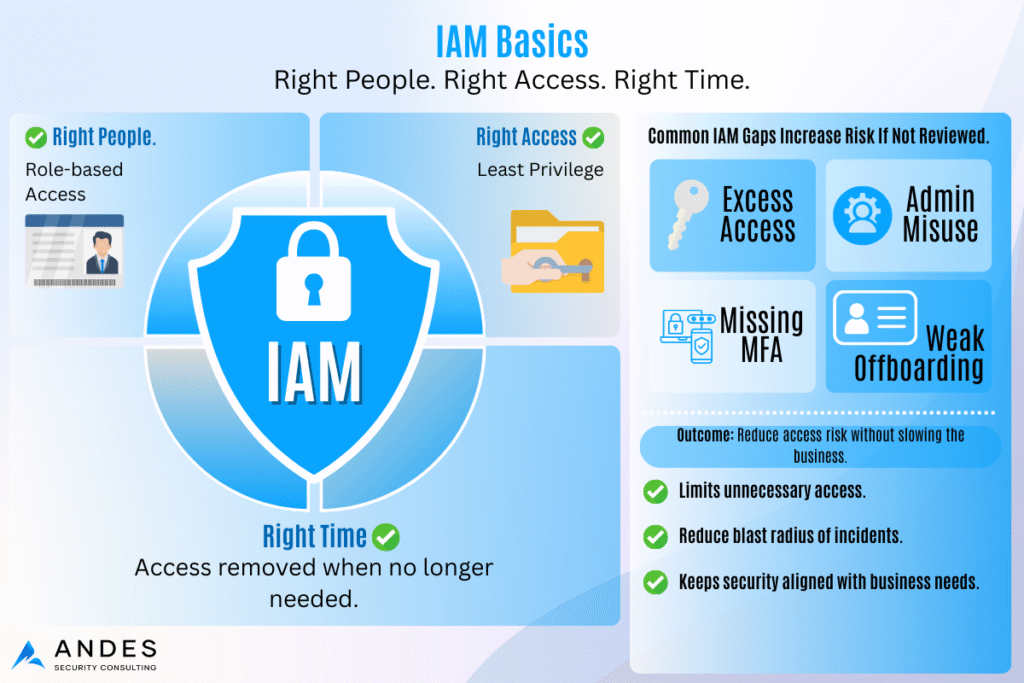
- Identity & Access
- Do all users and admins have MFA enabled?
- Are privileged accounts monitored and reviewed regularly?
- Devices
- Are devices patched and checked before connecting to company resources?
- Cloud & Network
- Are cloud configurations monitored for drift or misconfigurations?
- Is the network segmented to stop lateral movement?
- Data
- Is sensitive data classified and protected with least-privilege rules?
- Detection & Response
- Are logs centralized and monitored for suspicious behavior?
If the answer is “no” or “we’re not sure” — you’re operating without Zero Trust fundamentals.
How Andes Security Consulting Helps SMBs Implement Zero Trust
Andes Consulting specializes in helping small and mid-size organizations adopt practical, affordable Zero Trust strategies — without overwhelming your IT team.
We support clients through:
1. Zero Trust Maturity Assessment
A structured evaluation of your identity, network, cloud, data, and monitoring controls.
2. Quick-Wins Roadmap
Immediate steps to reduce risk, strengthen access controls, and close high-impact gaps.
3. Cloud & Identity Architecture
Implementation of secure cloud landing zones, IAM hardening, conditional access, and segmentation.
4. Policy & Governance Framework
Right-sized Zero Trust governance aligned to NIST CSF and industry best practices.
5. Managed Guidance & Oversight
We partner with your IT team to ensure controls stay effective as your business grows.
Zero Trust isn’t a product — it’s an approach. And SMBs that adopts this approach will gain stronger security, lower breach probability, and higher cyber resilience with predictable cost and effort.
Conclusion
Zero Trust is no longer a “big enterprise” initiative — it is now essential for small and mid-size firms facing modern cyber threats. Starting with identity, access, segmentation, and continuous verification, SMBs can dramatically reduce breach risk and strengthen operational resilience.
If you’re unsure where your organization stands or how to begin, Andes Security Consulting can guide you step-by-step.